Bot Detection power-up
Updated Jan 28, 2026
Overview
This power-up checks each incoming request for signs of bot activity. When enabled, it adds two headers to every request:
- X-Device-Bot (true or false).
- X-Device-Bot-Score (a score from 0 to 100).
The score helps you understand how suspicious the request is. A score between 50 and 75 means the request looks unusual, but we do not block it because the checked parameters do not fully confirm bot behavior. A score above 75 means all parameters match bot activity, and the request is blocked if blocking is enabled.
You can also create a Request Header variable in your server Google Tag Manager container to use these signals. This lets you filter out suspicious traffic or stop GA4 or other tags from firing when a request looks like bot traffic.
How to set up the Bot Detection power-up
1. Log in to your stape.io account.
2. Select your sGTM container on the dashboard.
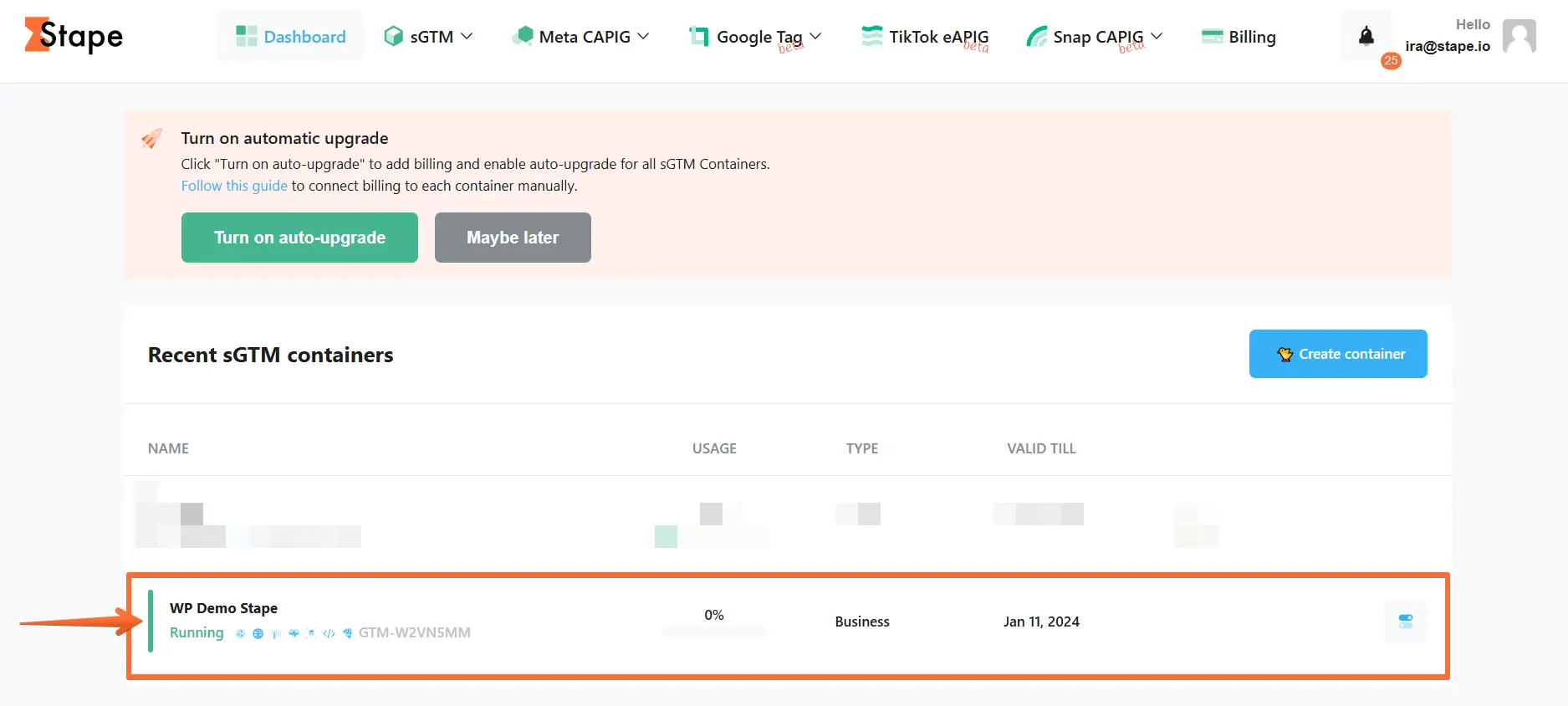
3. Click Power-ups, then click the Use button next to the Bot Detection panel.
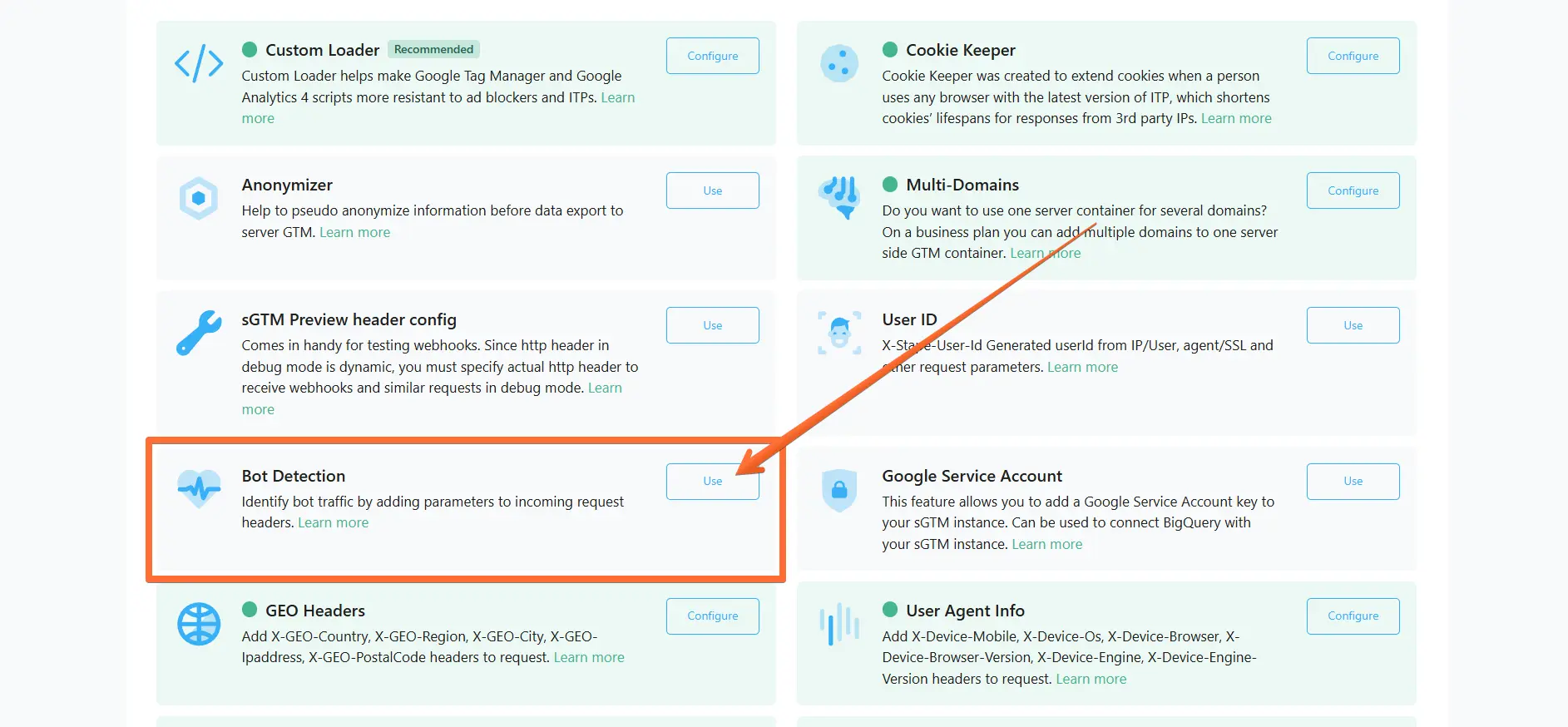
4. Toggle the Bot Detection switch.

5. Select one of the options:
- Add request headers - the power-up will add bot detection request headers to incoming HTTP requests.
- Block requests from bots - the power-up will filter out requests to vendors (e.g. GA4 /collect or Data Tag /data). If you select this option and are using Custom Loader, make sure to activate the Prevent web GTM load toggle to prevent web GTM load for bot/spam traffic.

6. Click Save changes.

7. The Bot Detection power-up has been configured on Stape. Here is an example of how to use the power-up’s data to filter the bot traffic in Google Tag Manager:
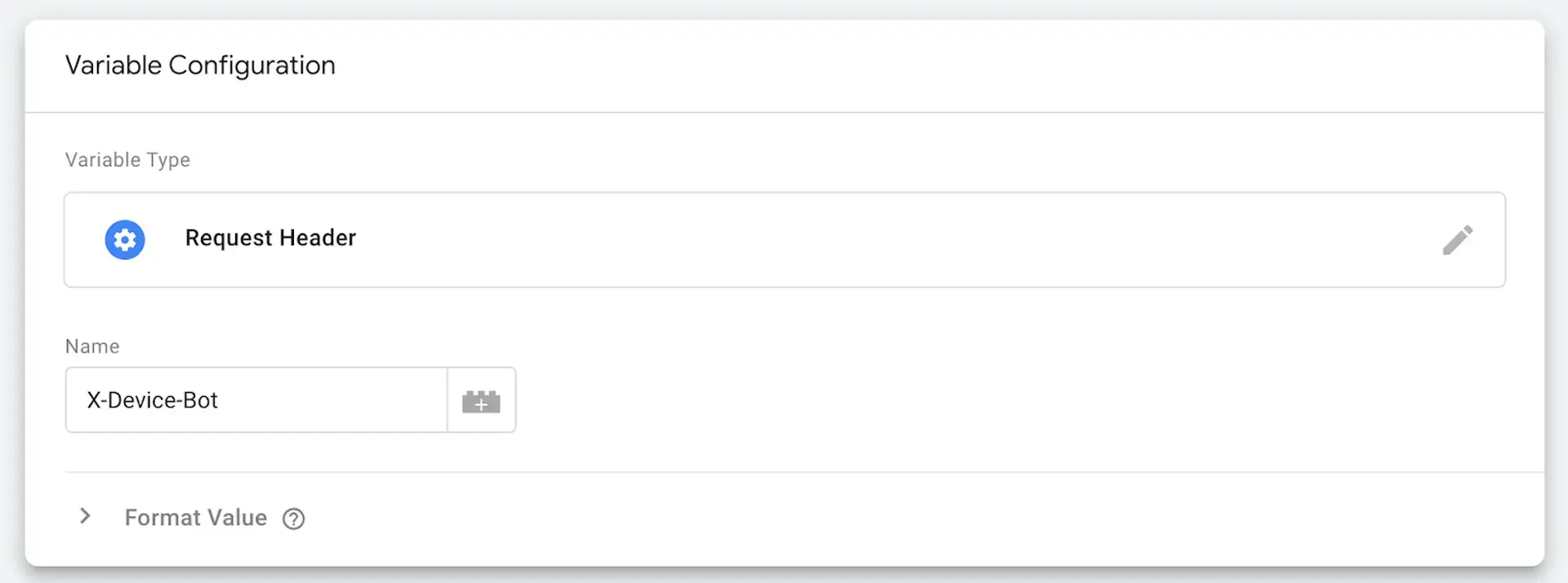
1) Create a Variable on the sGTM container with the type Request Header and enter the name X-Device-Bot.
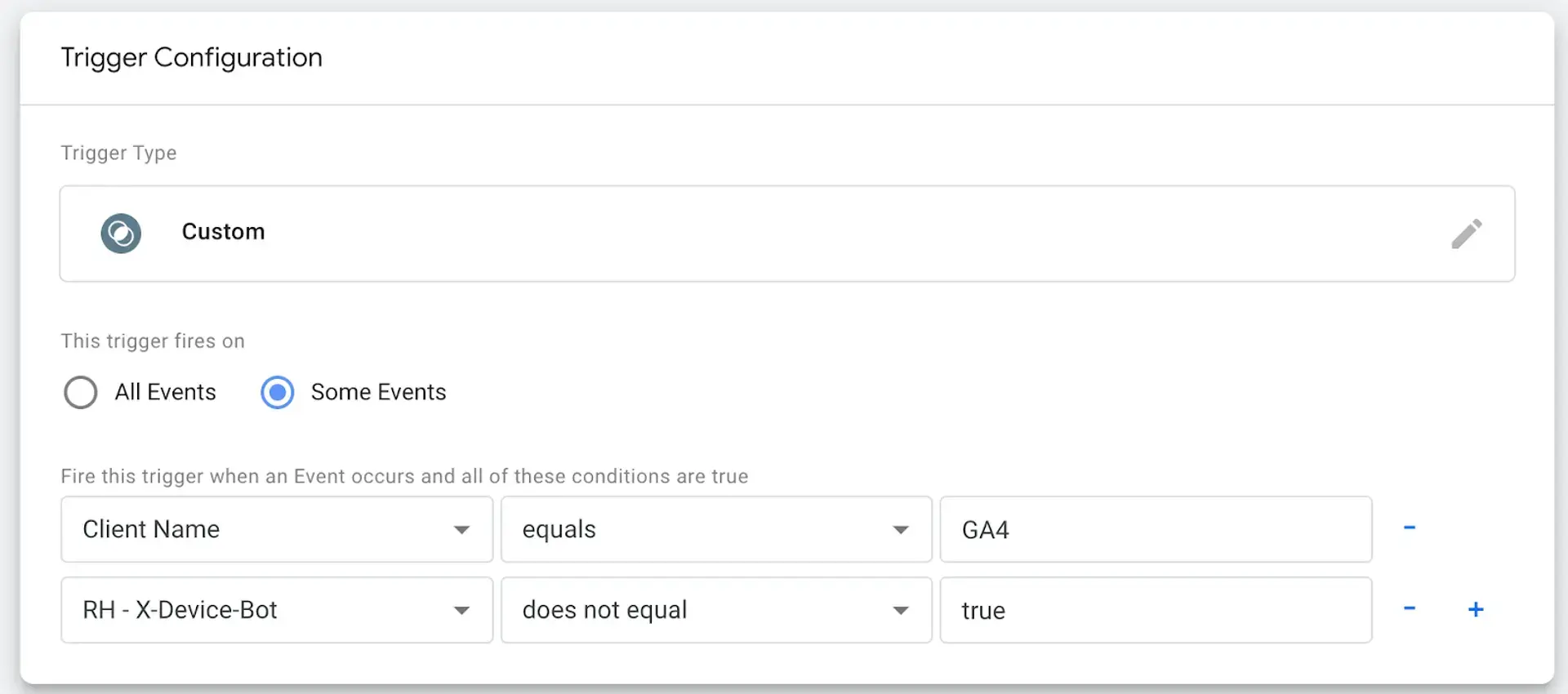
2) Use this variable as an additional condition in your GA4 trigger configuration on the server (or any other triggers where you want to limit the impact of bot traffic).
Testing Bot Detection
To verify that the Bot Detection power-up works correctly: open the server Google Tag Manager container preview → go to the Request tab → click on Incoming HTTP Request → click Show More in the Request Headers section. If you see the X-Device-Bot headers, everything is working properly.

If you're using the Block requests from bots option, you can use the Stape Logs feature to see filtered requests. You can filter blocked requests in Stape Logs by the 403 status code.

Other methods for detecting and excluding bot traffic
This section covers alternative ways to fight bot traffic:
These methods are less universal than Bot Detection. However, you can use one or both of them in conjunction with our power-up to achieve better results.
Cloudflare bot detection
If you use Cloudflare and most of your bot traffic comes from a specific country, you can activate Bot Check for IP addresses from that country. This is an effective solution, but only if you have no real visitors from that location, lest you affect the stats of real visits from there.
1. In your Cloudflare account, open the Security rules page → click Create rule → select Custom rules.
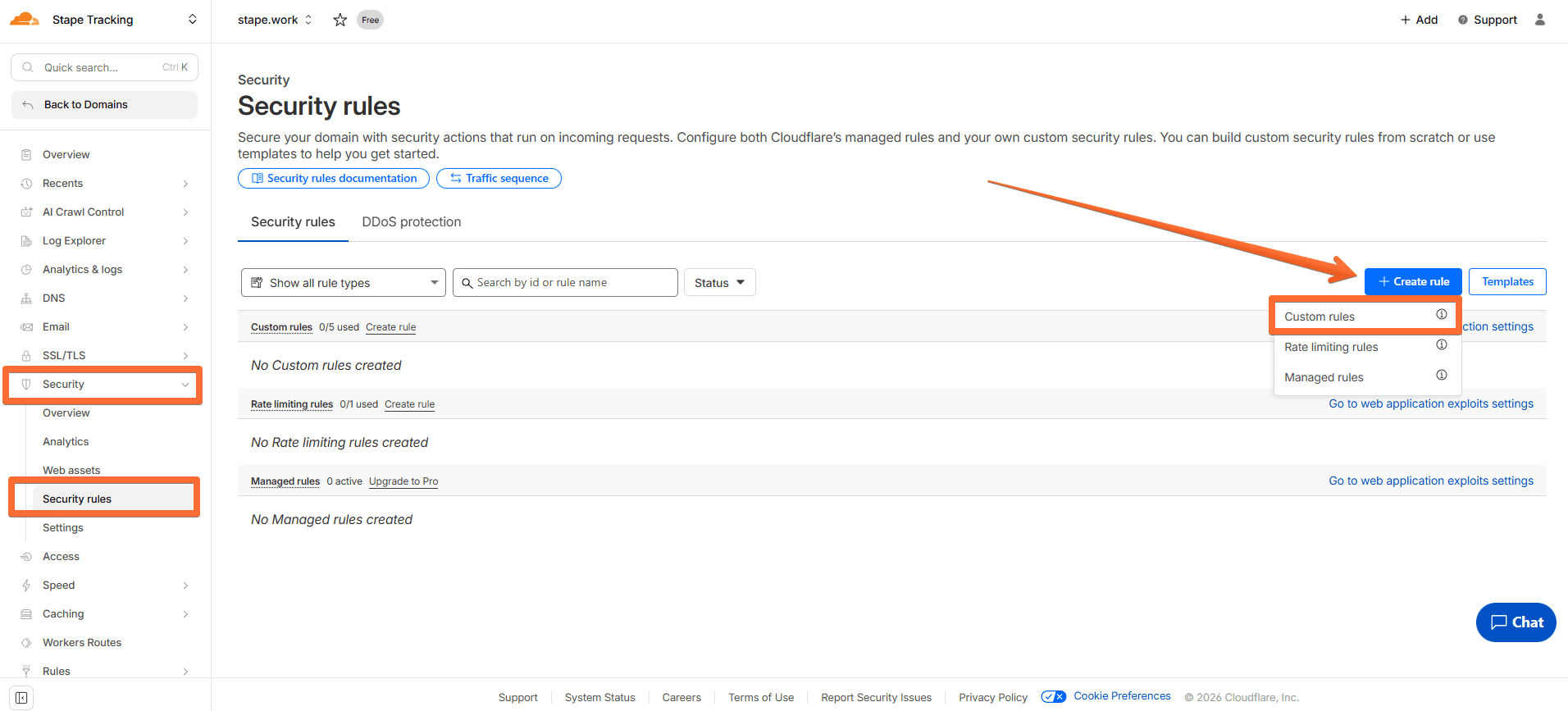
2. Configure the rule:
- Rule name - enter a descriptive name.
- Field - Country.
- Operator - equals.
- Value - select your bot traffic’s country of origin.
- Choose action - managed challenge.
Then click Deploy.
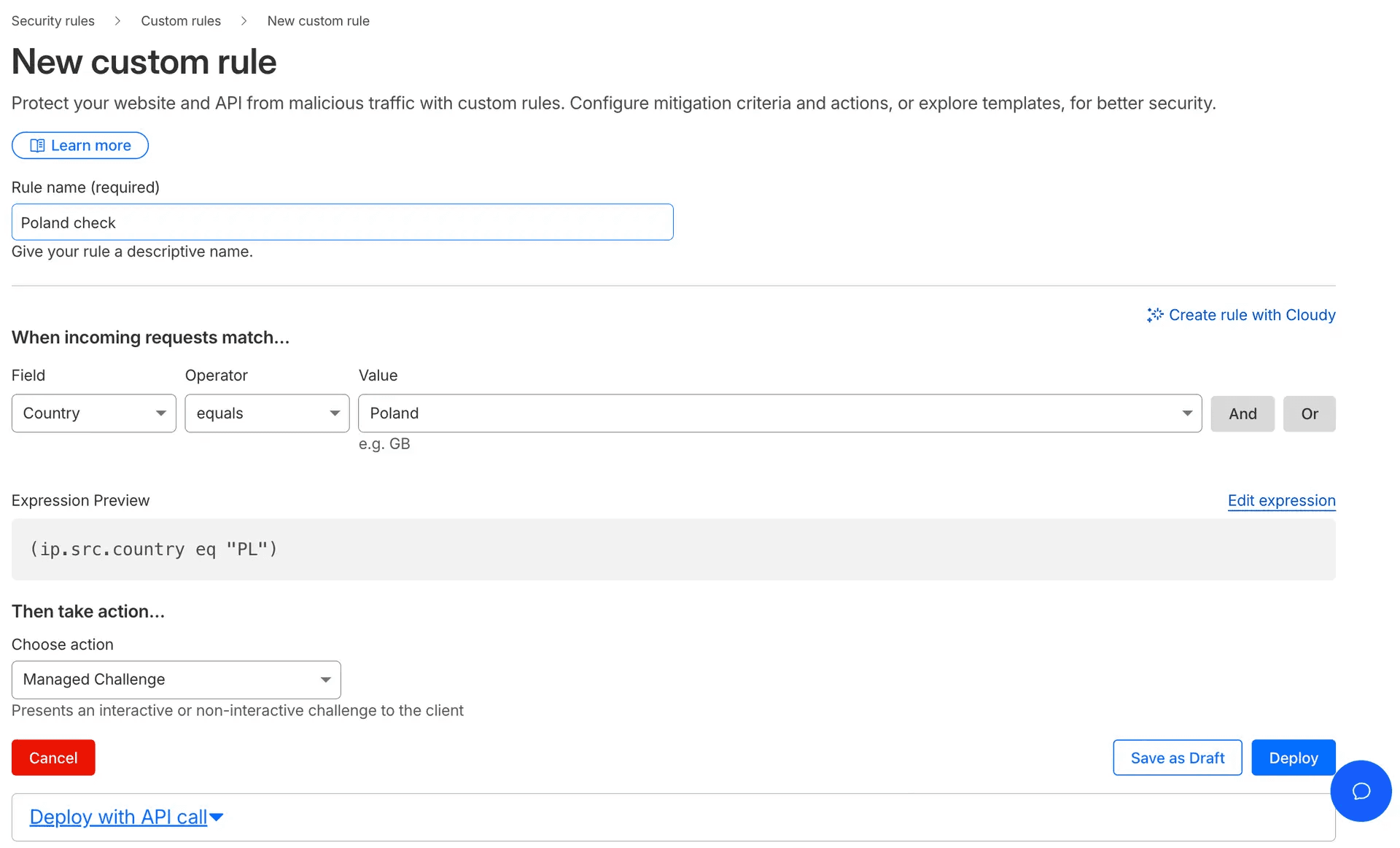
Other Cloudflare features to block bot traffic include:
- Known bots - will exclude the traffic from Cloudflare’s list of bots.
- Verified bot category - exclude bot traffic from the listed categories.
Block spam referrals on the trigger level
If the referral contains your spam domains, you can add an exception trigger for your GA4 tags:
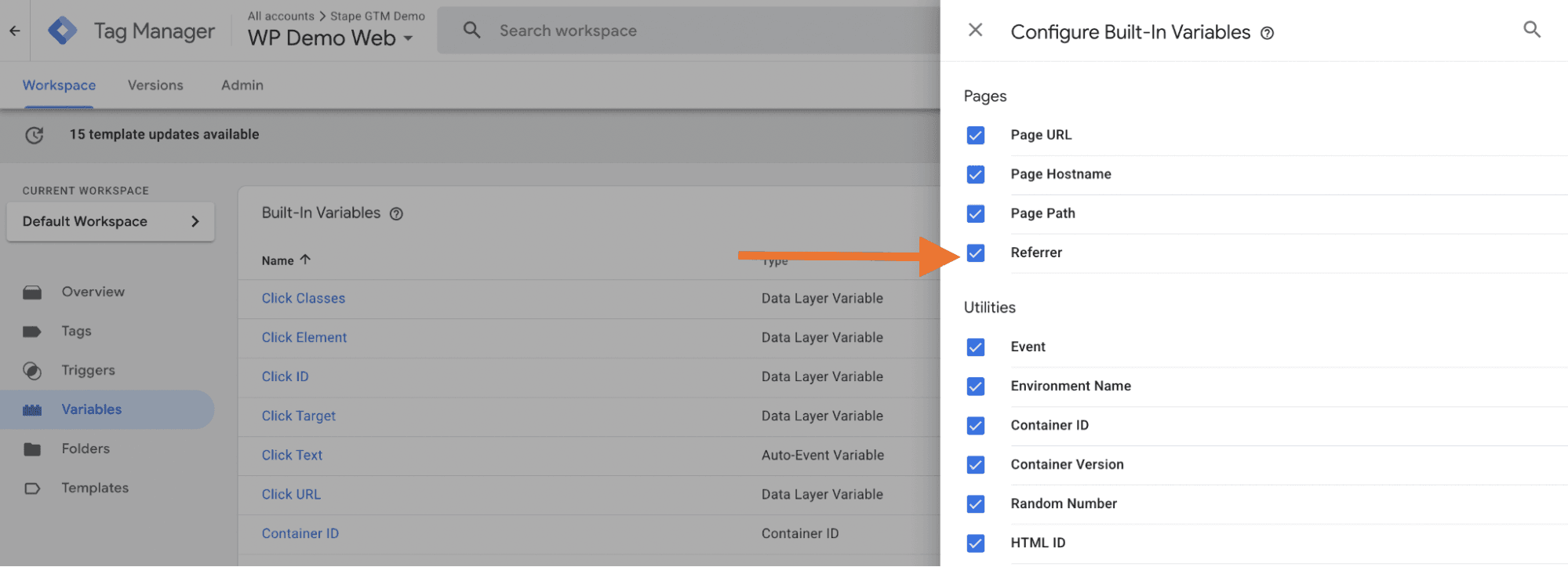
1. In your web GTM container, open the Variables menu → in your built-in variables, enable the Referrer variable.
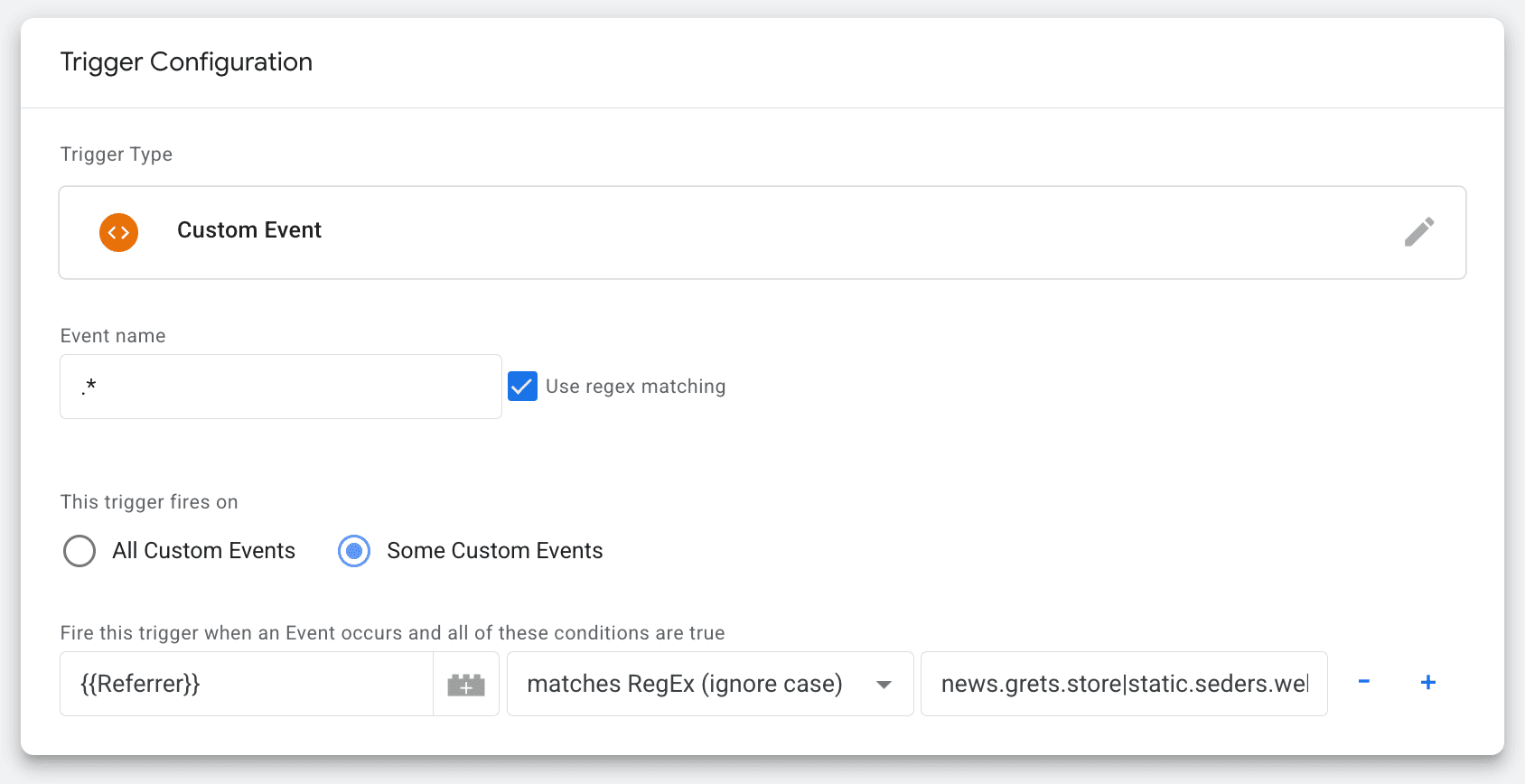
2. In the Tags menu, create a new Custom Event trigger that will work for any event (set the Event name to “.*” and check the Use regex matching box). Under This trigger fires on - select Some Custom Events.
Specify the condition for the trigger: {{Referrer}} - matches RegEx (ignore case) - enter your spam domains. For several domains, use “|” without spaces (e.g.: news.grets.store|static.seders.website|another.domain)
3. Add this trigger as an exception to your GA4 tags. Go to the Tags menu → select a tag → under Triggering, click Add Exception → select the trigger from the previous step.
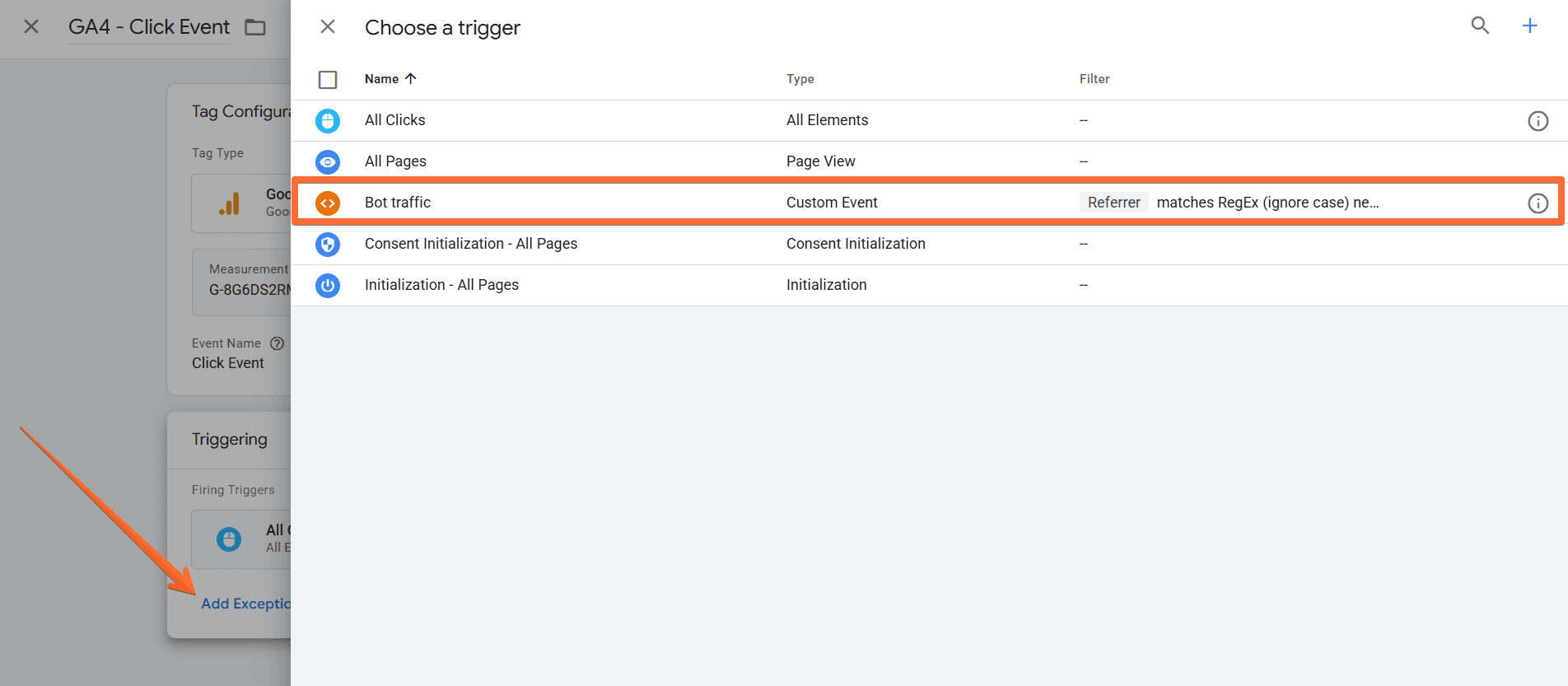
Publish the changes on your container. The exception trigger will prevent the tags from working if the referral contains one of your spam domains, and this data will not be included in GA4.
Comments